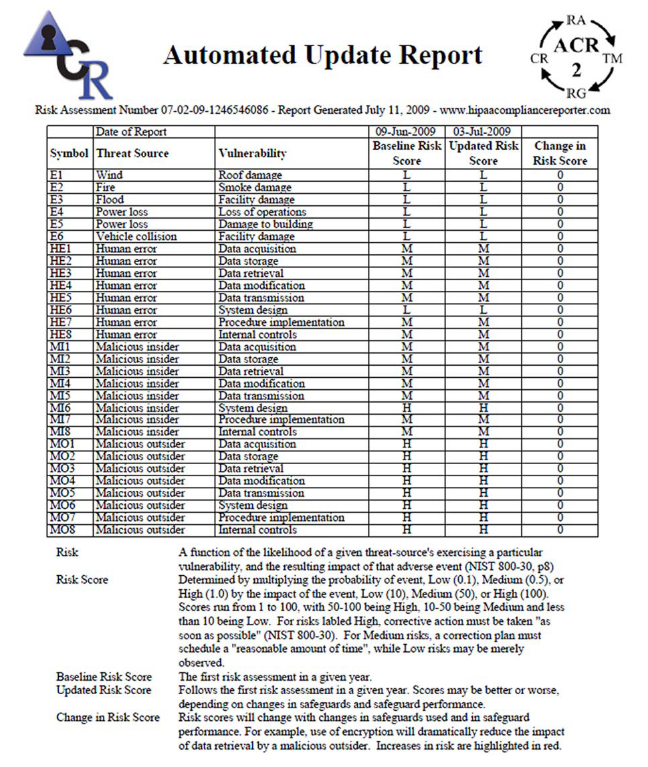
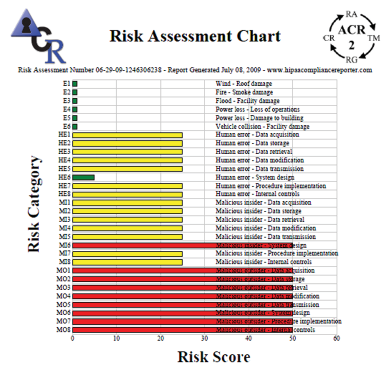
ACR 2 Basic
Automated Compliance Reporting 2
Automated Compliance Reporting 2 (ACR2) is a family of interrelated
software packages that allow automated updating of mandatory
compliance reports for the twenty million organizations
regulated under any combination of the below four regulations:
- Gramm Leach Bliley Act (GLBA) of 1999
- Health Insurance Portability and Accountability Act (HIPAA)
of 1996
- Payment Card Industry Data Security Standard (PCI) of 2006
- The Federal Information Security Management Act (FISMA)
of 2002
There is significant confusion about the dividing line between
compliance and security. They are related but distinct. Compliance
involves meeting the "standard of care" set by whatever
regulatory authority oversees an organization. Security is keeping
unauthorized persons away from accessing, corrupting or destroying
sensitive data.
|
What are Organizations Legally Required to Do About Information Security?
More than 20 million organizations worldwide are regulated under GLBA, HIPAA or PCI information security requirements.
None of these regulations require organizations to be perfectly secure. All of these regulations require
organizations to be compliant with similar, specific rules and regulations. There are penalties for non-compliant
purchase card (PCI) vendors can be penalized or disqualified from handling credit cards. Enforcement of information
security regulations is increasing, driven by significant political pressure and epidemic of identity theft.
|
For Any Security Compliance Program, Risk Assessment is the Beginning
GLBA, HIPAA and PCI all require regulated companies to perform a risk assessment and then take "appropriate"
precautions against "reasonably foreseeable" risks. For example quoting from the Gramm Leach Bliley Act (GLBA):
"Information security program.. You shall develop, implement and
maintain a comprehensive information security program ... Appropriate
to your size... Identify reasonably foreseeable> internal and
external risks... and assess the sufficiency of any safeguards in place...
At a minimum, such a risk assessment should include... (1) Employee
training and management; (2) Information systems, including.. (3)
Detecting, preventing and responding to attacks, intrusions, or other
systems failures... Design and implement information safeguards to
control the risks you identify through risk assessment, and regularly
test.." (emphasis added)
|
|
In the case of HIPAA, GLBA and PCI, there are five common compliance requirements. These regulations
require organizations to:
- perform a risk assessment
- setup an information security plan
- install and test the installed safeguards
- revise the risk assessment accordingly
- report the test results
This process is shown graphically below.
The next step in compliance is to determine how
to perform the necessary steps. The National Institute of Standards and Technology (NIST) has published a
series of protocols that govern risk assessments and minimum precautions for government systems. These
protocols are mandatory for use by the FDIC and other Federal regulators, and recommended for financial and
medical companies by such regulators as FFIEC and CMS. The protocols are also long, complex and confusing.
For example more than 90 NIST protocols relate to minimum safeguards under FISMA.
|
The ACR2 Solution
ACR 2 Solutions, Inc. has created a product that does to compliance regulations what tax
programs do to Federal and State tax law. We have converted complex regulations into a
straightforward fill-in-the-blank software package. These programs meet the risk assessment
and updating tasks required under GLBA, HIAA, and PCI DSS and similar regulations
(see items 1, 4, and 5 in the diagram above). Step 2, setting up security programs
based on the risk assessment. This is where our included gap report and supplemental
guidance can help your IT staff or MSP prioritize. Step 3. Installing and testing safeguards
A key element in using ACR2 solutions is that all the safeguards and protocols
used by the ACR2 progams are based on Federal recommendations and requirements.
The programs reporters have been audited and accepted by the OCC and the FFIEC.
Getting Started
To use ACR2Basic
just browse to our
website and enter
your user-id and
password and start
answering the
questions. When
you complete the
questionnaire press
the finalize button.
Your encrypted pdf
reports are emailed
to you. It couldn't
be faster or easier!
|